Using Token2 FIDO2 security keys as the default sign-in option for Windows (Registry modification method)
FIDO2 based Passwordless technology allows users to use a USB key to sign in to Azure AD (Microsoft Entra ID) without using passwords.Once enabled, the users will be able to sign in to their accounts and log onto their Azure-joined machines using FIDO2 Security keys.
The access is still protected by two factors in this case:
1) having physical access to the security key and
2) PIN or Fingerprint (on devices with biometrics support) configured on the FIDO2 Security keys
The guide below will walk you through the steps required to enable Token2 FIDO2 Security keys as the default sign-in option for Windows. Please note that this guide uses local registry modifications method and does not require Intune. Intune-based method is described here.
Requirements:
• An Azure-joined Computer with Windows 10 - 1903 or higher.• A Token2 FIDO2 key, and a user with FIDO2 key associated (check this article for instructions on enrolling FIDO2 security keys)
• A local administrator privilege on the machine
Check Azure AD (Microsoft Entra ID) joining status
To check if the devices are Azure AD (Microsoft Entra ID) joined or not, you can open cmd and run dsregcmd /status
If the device is Azure AD (Microsoft Entra ID) joined, the status for AzureAdJoined=Yes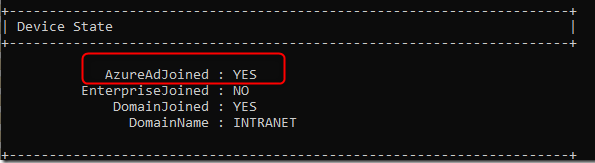
To enable security key sign-in using Group Policy, you can follow these steps:
- Press the Windows key and type
gpedit. - Right-click on the result and choose "Run as administrator."
- When prompted to run the app in elevated mode, select "Yes."
- Go to
Computer Configuration > Administrative Templates > System > Logon.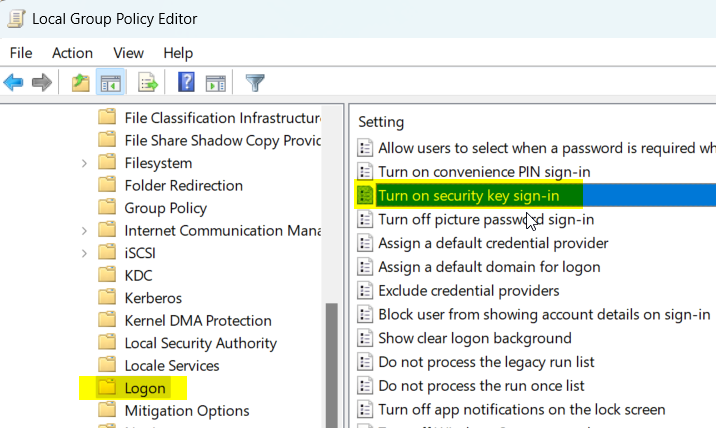
- Double-click on "Turn on security key sign-in" and choose "Enabled." Then click "OK."
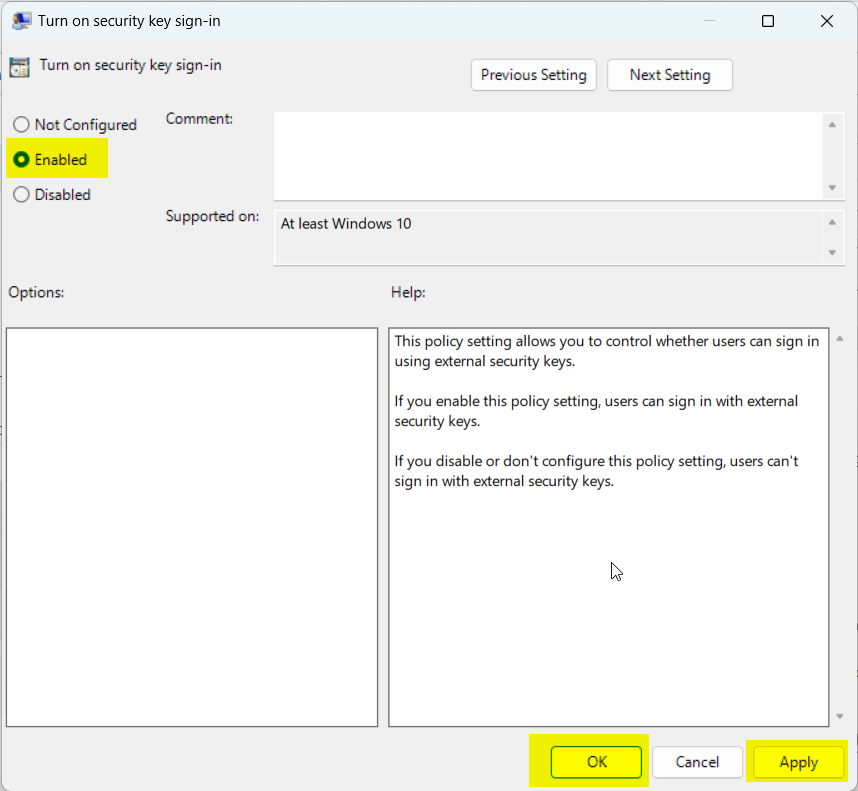
- Close the Group Policy Editor and restart your computer to apply the changes
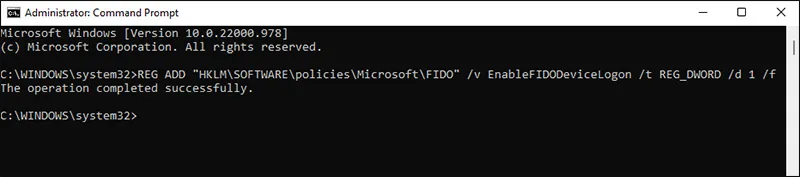
The same operation can be achieved using the command below:
REG ADD "HKLM\SOFTWARE\policies\Microsoft\FIDO" /v EnableFIDODeviceLogon /t REG_DWORD /d 1 /f
Entra Passwordless
- Automated Registration for Entra ID with PowerShell and GraphAPI
- Enrollment guide (standard)
- Enrollment guide (using Temporary Access Pass)
- Configure workstation passwordless login (Intune method)
- Configure workstation passwordless login (registry modification method)
- Configuring iPhone Mail apps for users only with Passwordless access
- Default MFA Method for Microsoft Entra ID
Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!
