Passwordless authentication in Azure AD with Token2 FIDO2 keys
FIDO2 based Passwordless technology allows users to use a USB key sign in to Azure AD (Microsoft Entra ID) without using passwords. Once enabled, the users will be able to sign in to their accounts and log onto their Windows 10 machines ( Azure AD (Microsoft Entra ID) or Hybrid AD joined ) using FIDO2 Security keys. The access is still protected by two factors in this case: 1) having physical access to the security key and 2) PIN or Fingerprint (on devices with biometrics support) configured on the FIDO2 Security keys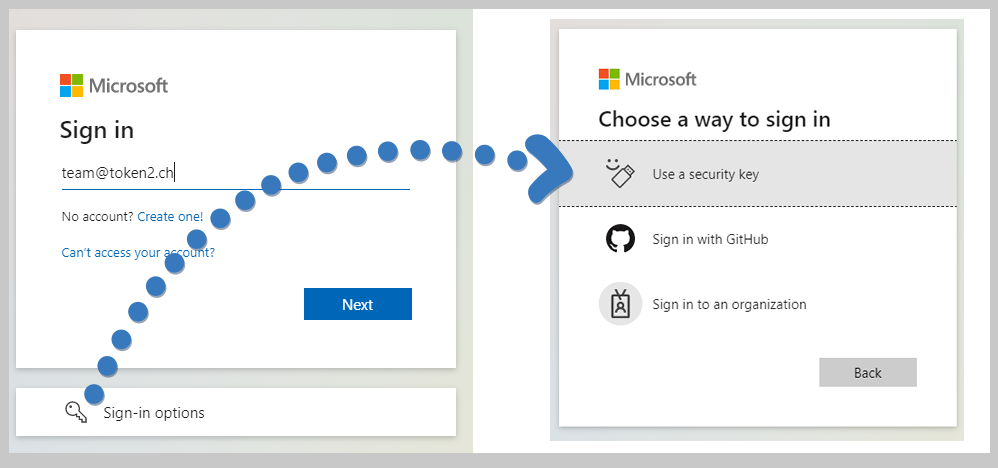
In the context of Azure AD (Microsoft Entra ID), FIDO2 Security keys are not a replacement of the standard authentication mechanisms, they are added as an alternative, marketed by Microsoft as one of the Passwordless login methods. Also note that there were changes introduced by Microsoft during the Ignite 2021 conference as described on this page.The guide below will walk you through the steps required to enable passwordless access using Token2 FIDO2 Security keys.
Requirements
- An Azure AD (Microsoft Entra ID) tenant which licensed to use Azure MFA functions
- A global tenant admin account in Azure AD (Microsoft Entra ID)
- A regular account to use for the test
- A FIDO2 compatible security key, any Token2 FIDO2 Keys can be used
- Windows 10 - 1903 or higher. Only browsers supporting FIDO2 keys can be used as the during enrollment and sign-in
Enable FIDO2 authentication method
Log in to your tenant admin interface and navigate to Azure Active Directory → Security → Authentication methods.
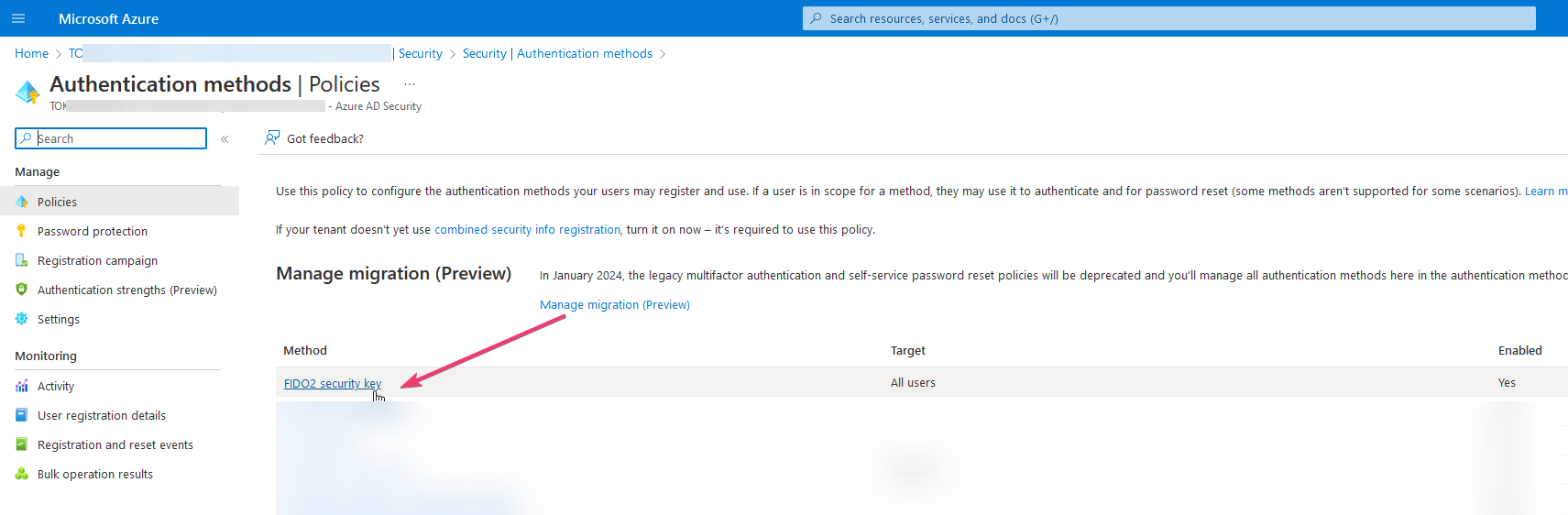
Click on "FIDO2 Security Key" and then select "Enable" and "All Users"
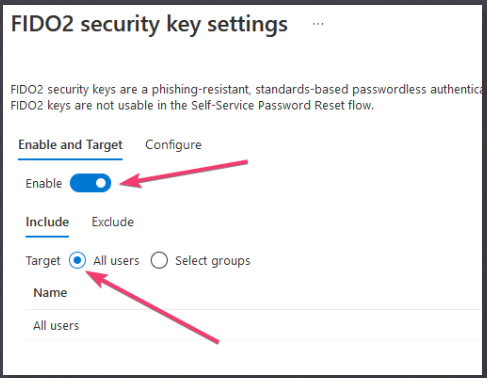
After the authentication method has been activated, users are able to enroll their FIDO2 Keys.
User registration and management of FIDO2 security keys
Note that only end users can perform the enrollment. Administrator provisioning and de-provisioning of security keys is not available in the public preview.
- Browse to https://myprofile.microsoft.com
- Sign in if not already
- Click Security Info
- If the user already has at least one Azure Multi-Factor Authentication method registered, they can immediately register a FIDO2 security key.
- If they don’t have at least one Azure Multi-Factor Authentication method registered, they must add one. Alternatively, you can use Temporary Access Pass method (this will allow using FIDO2 keys without setting a password for the user).
- Add a FIDO2 Security key by clicking Add method and choosing Security key
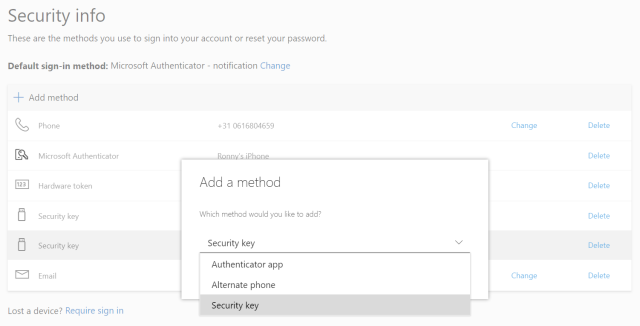
- Choose USB device
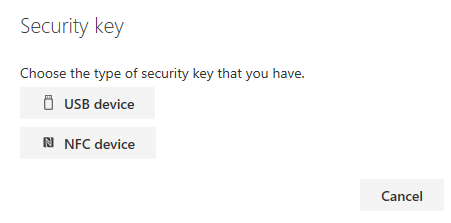
- Have your key ready and choose Next
- A box will appear and ask you to create/enter a PIN for your security key, then touch the shield or lock icon on the key (the LED indicator is usually blinking at this moment). If the PIN code for your FIDO2 key has already been set, it will ask to enter it. Please note that for biometric-enabled keys, PIN can be replaced by a fingerprint authentication.
- You will be returned to the combined registration experience and asked to provide a meaningful name for your token so you can identify which one if you have multiple. Click Next.
- Click Done to complete the process
Changing the PIN and resetting the Security Key
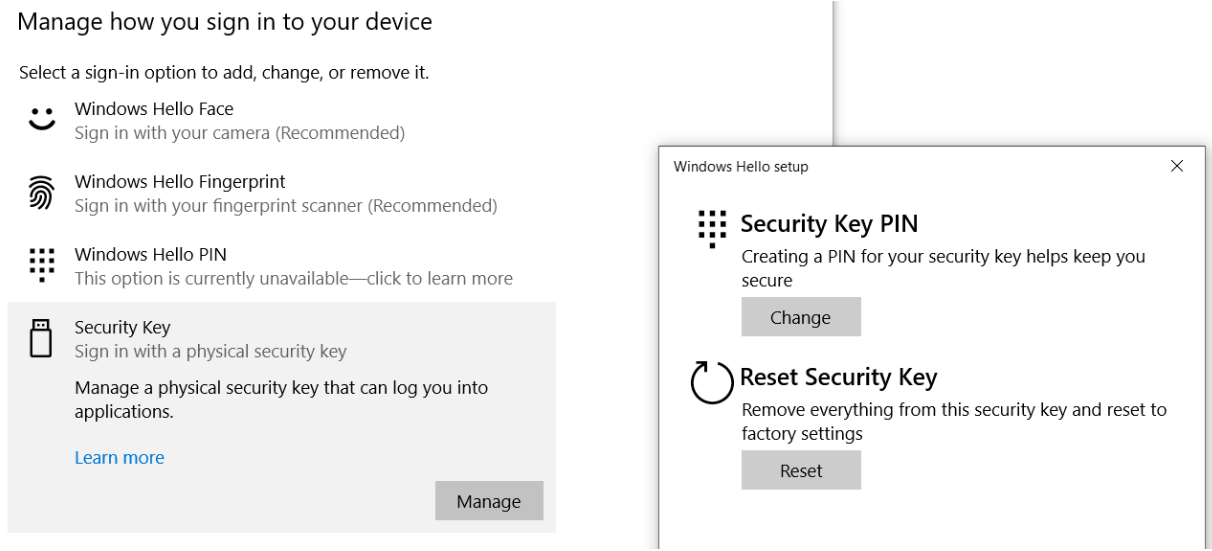
Azure AD (Microsoft Entra ID) requires the security keys to be protected with a PIN code. This can be done during the enrollment, but you can also change the PIN code later if needed. In case you forgot the PIN code, you can reset the security key and re-enroll again (as a new FIDO2 Security device). Changing the PIN and resetting Token2 T2F2 security keys can be done using the Windows Control panel (Control Panel -> Windows Security -> Account Protection -> Windows Hello / Manage sign-in options -> Security Key -> Manage )
Video
Check out this video review demonstrating the process of the configuration of this method as well as user registration and login experience- Automated Registration for Entra ID with PowerShell and GraphAPI
- Enrollment guide (standard)
- Enrollment guide (using Temporary Access Pass)
- Configure workstation passwordless login (Intune method)
- Configure workstation passwordless login (registry modification method)
- Configuring iPhone Mail apps for users only with Passwordless access
- Default MFA Method for Microsoft Entra ID
Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!
