Using Token2 FIDO2 security keys as the default sign-in option for Windows (Intune method)
FIDO2 based Passwordless technology allows users to use a USB key to sign in to Azure AD (Microsoft Entra ID) without using passwords.Once enabled, the users will be able to sign in to their accounts and log onto their Azure-joined machines using FIDO2 Security keys.
The access is still protected by two factors in this case:
1) having physical access to the security key and
2) PIN or Fingerprint (on devices with biometrics support) configured on the FIDO2 Security keys
The guide below will walk you through the steps required to enable Token2 FIDO2 Security keys as the default sign-in option for Windows. Please note that this guide uses Intune enrollment. Having Intune is not a requirement, you can achieve the same using registry modification method.
Requirements:
• An Azure-joined Computer with Windows 10 - 1903 or higher.• An Azure AD (Microsoft Entra ID) tenant which licensed to use Azure MFA functions (Intune license is needed for this particular guide)
• A Token2 Fido2 key
• A local administrator privilege on the machine
Check Azure AD (Microsoft Entra ID) joining status
From PC
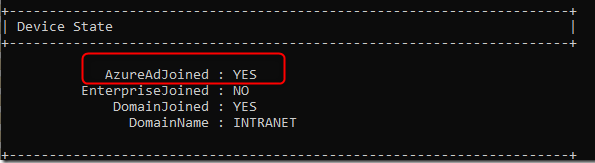
To check if the devices are Azure AD (Microsoft Entra ID) joined or not, you can open cmd and run dsregcmd /statusIf the device is Azure AD (Microsoft Entra ID) joined, the status for AzureAdJoined=Yes
From Azure
Log in to your Azure portal and navigate to Azure Active Directory → Devices → All devices.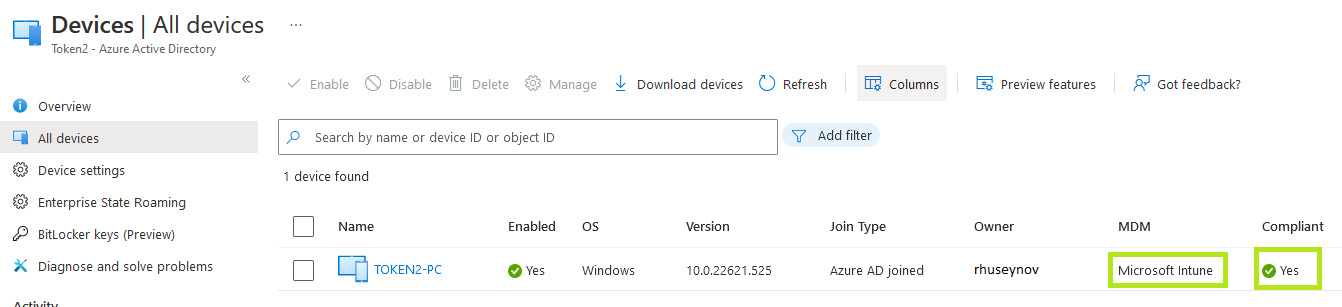
If you have successfully activated the Intune license and assigned it to the user, you get the Microsoft Intune value for the MDM column.
Also, be sure that the Compliant column has an OK value.
If these two conditions are observed, the device will appear and be ready to use in the Microsoft Intune Admin Center.
User registration of FIDO2 security keys
• Browse to https://myprofile.microsoft.com• Click Security Info
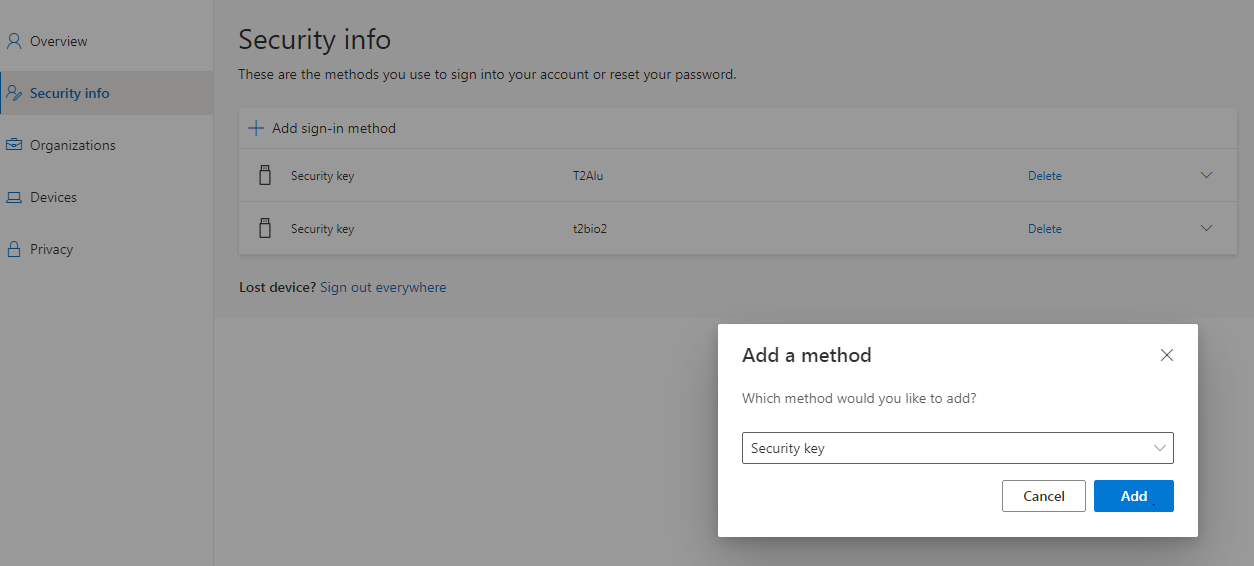
• Add a FIDO2 Security key by clicking Add method and choosing Security key
• Choose USB device
• Have your key ready and choose Next
• A box will appear and ask you to create/enter a PIN for your security key. Touch the shield or lock icon on the key (the LED indicator is usually blinking at this moment).
• If the PIN code for your FIDO2 key has already been set, it will ask to enter it. Please note that for biometric-enabled keys, PIN can be replaced by a fingerprint authentication.
• You will be returned to the combined registration experience and asked to provide a meaningful name for your token so you can identify which one if you have multiple. Click Next.
• Click Done to complete the process.
Enable security key sign-in with Endpoint Manager
Microsoft Endpoint Manager AKA Intune can be used to easily enable security key sign-in for managed devices.1) Open a browser and navigate to Microsoft Intune
2) Log in as an administrator
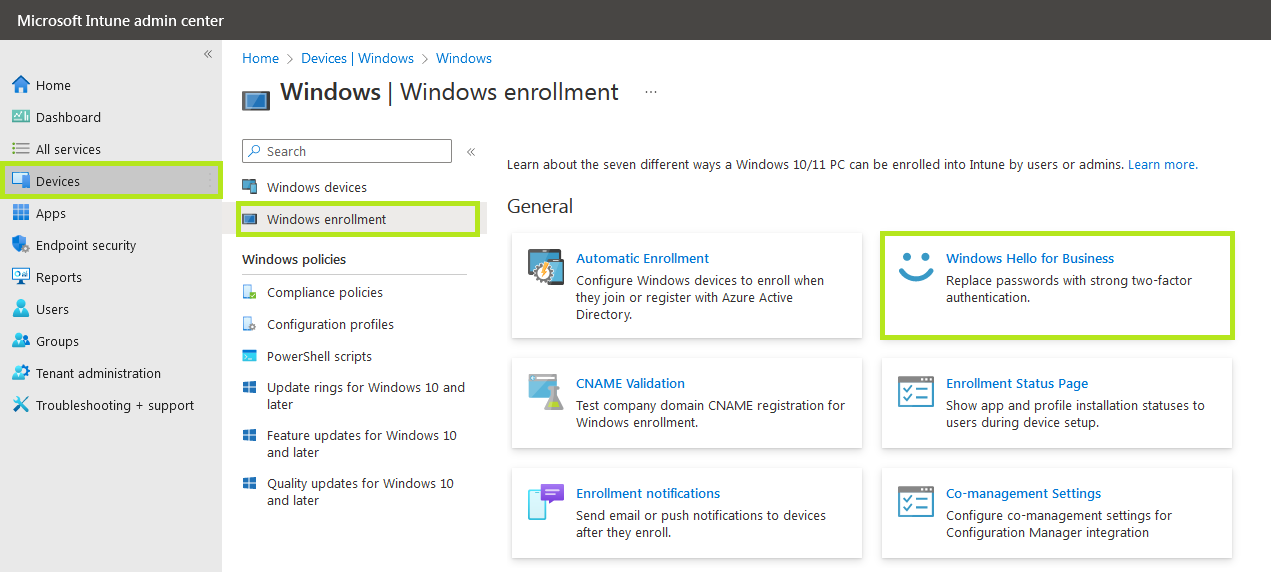
3) Click on Devices in the panel left hand side
4) Next, navigate to Windows and Windows Enrollment
5) Click on Windows Hello for Business
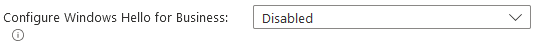
6) Scroll down and set 'Configure Windows Hello for Business' to Disabled and ‘Use security keys for sign-in’ to Enabled

7) Click Save and then close the panel.
8) Restart your PC. After that, you will see a logon screen as below.
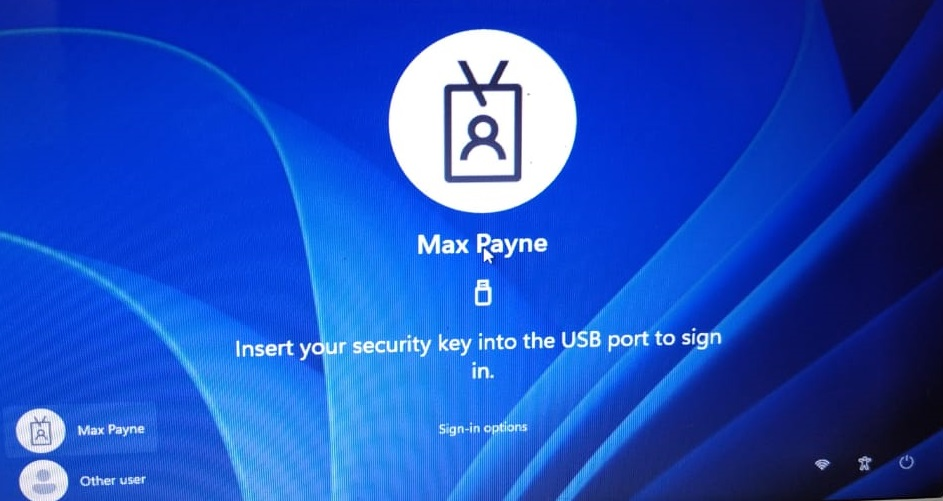
9) If you insert the Fido2 key without fingerprint protection, you will be prompted to enter a PIN. In the case of a security key with fingerprint protection, this step does not occur.
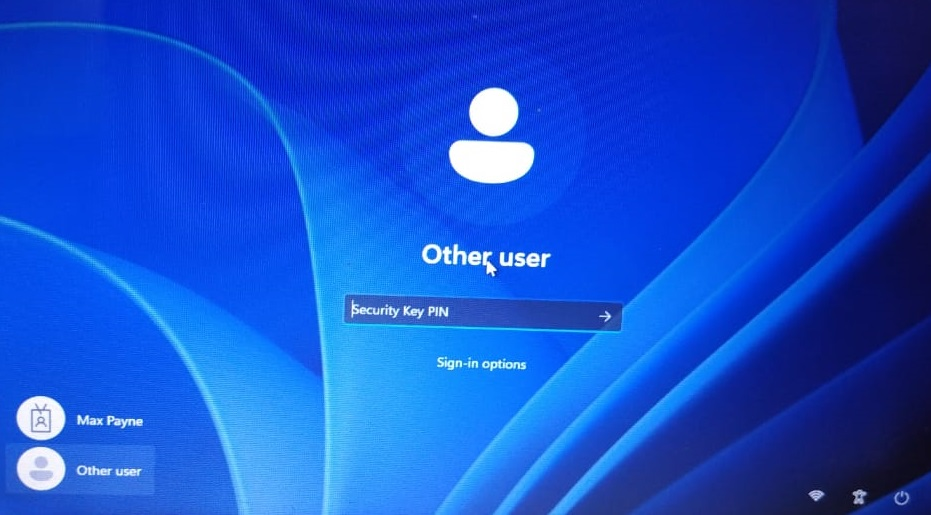
10) Touch the security key to continue.
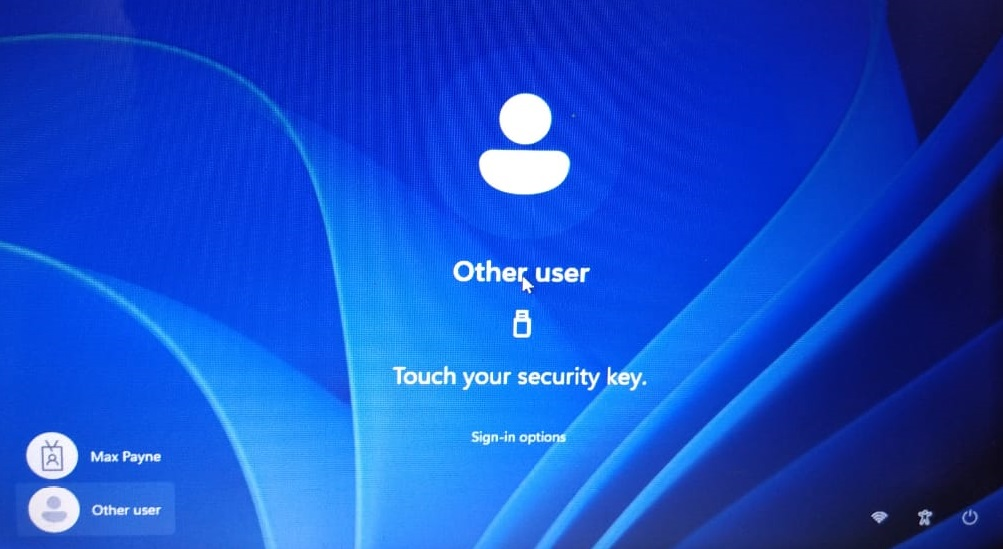
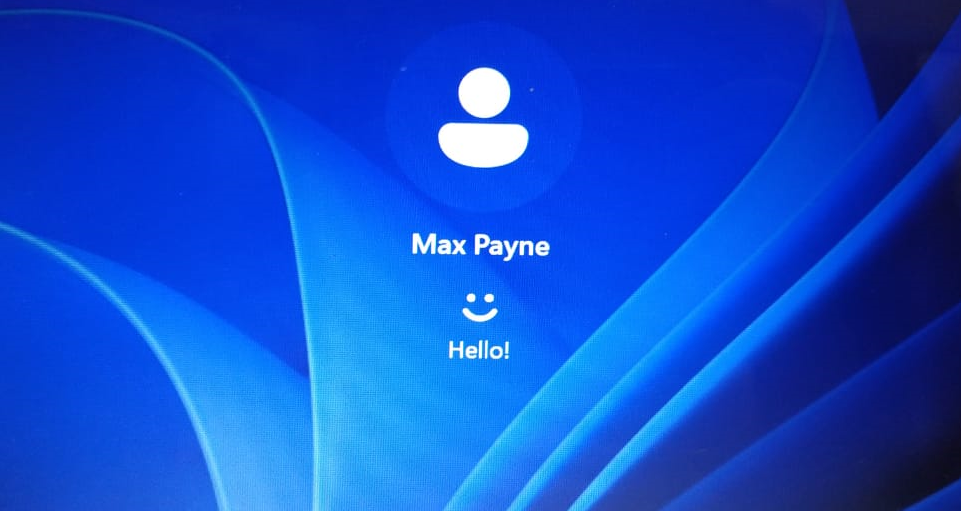
11) Now you can successfully login to your Azure AD (Microsoft Entra ID) user account.
Entra Passwordless
- Automated Registration for Entra ID with PowerShell and GraphAPI
- Enrollment guide (standard)
- Enrollment guide (using Temporary Access Pass)
- Configure workstation passwordless login (Intune method)
- Configure workstation passwordless login (registry modification method)
- Configuring iPhone Mail apps for users only with Passwordless access
- Default MFA Method for Microsoft Entra ID
Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!
