TOTPRadius VPN Portal - Client Authentication flow
No special VPN client installation is required for VPN Portal-based authentication to function, although we have released a special VPN helper app to simplify the user experience and make the process as fast as possible; one click will be enough to establish a VPN link. The VPN Portal will support systems relying on standard VPN protocols (LT2TP and L2TP/IPSec), such as Meraki Client VPN and Fortinet VPN solutions.The data flow diagram below illustrate the principle of the VPN Portal
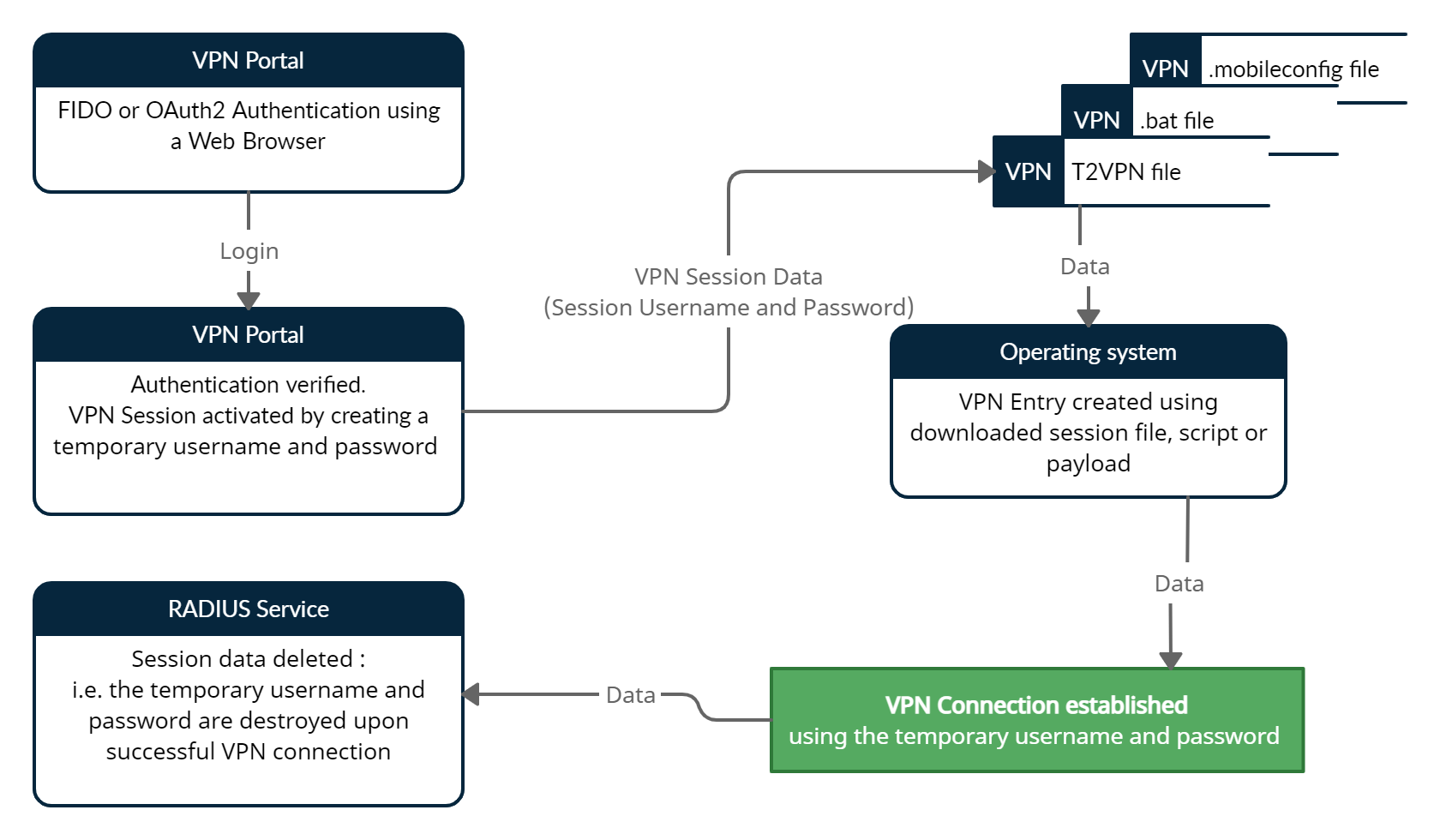
User logs in to a web interface where several files are generated. The user chooses to download a file named username.t2vpn and double-clicks on it (in some browsers it is possible to configure to "always open the file of this type" - this will save an extra click). If installed, our VPN Helper app (T2VPN) launches, parses the t2vpn file, extracts the VPN info (host, connection type, username and password) and initiates VPN connection. Once the connection is successful, the t2vpn file is removed for security purposes. Here is how the process looks like under Windows 10:
Using T2VPN app is optional, there are possibilities to use a batch file for Windows, or .mobileconfig files for iOS and MacOS machines - however executing these options require additional user actions.
About
Installation and configuration
- Installation and initial configuration
- Network configuration
- Migrating from older versions
- LDAP Configuration
- Azure AD Configuration
- Self-service enrollment portal
- Web and LDAPS Certificates
- Syslog configuration
- Single-factor authentication exceptions
- Slave appliance mode
- Dynamic RADIUS Attributes
Integration guides
Blog
21-12-2025
Android, NFC, and the Missing Piece of WebAuthn
 For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
19-12-2025
Streamline Token2 Classic Tokens in Okta
 Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
09-12-2025
Framework ExpansionCard Enclosure for Token2 Keys
 Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
