FIDO2 Token Management Tool - fido2-manage.exe
Overview
The FIDO2 Token Management Tool (fido2-manage.exe) is a command-line wrapper tool designed to interact with the libfido2 tool, providing a convenient way to perform various operations related to FIDO2 tokens.
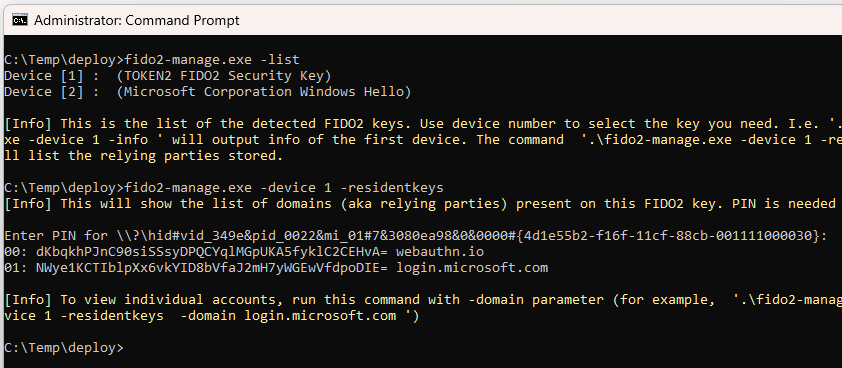
Running the tool
Open command prompt as administrator and navigate to the directory containing the tool. Execute the tool by running the following command:
.\fido2-manage.exe [parameters]Tool Parameters
The tool supports the following parameters:
-list: List available devices. Please note that if you plug in only one FIDO2 device, the device number to be used is always 1-info -device [number]: Retrieve information about a specific device.-storage -device [number]: Retrieve storage for credentials on a specific device.-residentKeys -device [number]: Retrieve a list of the relying parties on the device.-residentKeys -device [number] -domain [domain]: Retrieve resident keys on a specific device for individual accounts or relying parties in the specified domain.-delete -device [number] -credential [credential]: Delete a credential on a specific device with the specified credential ID.-uvs -device [number]: Enforce user verification to be always requested on a specific device.-uvd -device [number]: Disable enforcing user verification to be always requested on a specific device.-changePIN -device [number]: Change PIN of a specific device.-setPIN -device [number]: Set a PIN of a specific device (for new or freshly reset devices).-reset -device [number]: Performs a factory reset of a specific device (please note that this operation has to be performed within 10 seconds after plugging the key in. Important: factory reset will remove all configuration, including all passkeys and current PIN code). Please note that this action resets only the FIDO applet and does not affect the TOTP or GPG applets on the same key, if present.-forcePINchange -device [number]: To enforce PIN change for a specific device. The existing PIN is required solely for setting a new PIN; no other operations with the existing PIN are possible. Additionally, the GUI tool remains disabled until a new PIN is established. This operation will ask for a PIN to be entered; to avoid it, specify-pinargument-setMinimumPIN [minimum] -device [number]: parameter ensures that PINs meet a defined minimum length requirement. Example:fido2-manage.exe -setminimumPIN 13 -device 1sets the minimum to 13 characters. This parameter can be only increased and not decreased. Resetting the key to factory setting reverts this value to its default (4 for regular keys, 6 for PIN+ series, 8 for PIN+ Octo etc.)-fingerprint -device [number]: Enrolls a fingerprint for a specific device. The tool requires 4 samples of the same finger to complete the process.-fingerprintlist-device [number]: Lists enrolled fingerprints of a specific device-deletefingerprint ID -device [number]: Deletes an enrolled fingerprint from a specific device. Here, ID represents the number of the fingerprint to be deleted (as displayed in the fingerprintlist option).-renamefingerprint IDName a fingerprint slot by its ID-fingerprintname -device [number]
Biometric Key Options
Examples
-
List available devices:
.\fido2-manage.exe -list -
Retrieve information about a specific device:
.\fido2-manage.exe -info -device 1 -
Retrieve storage data for credentials (number of resident keys stored and available) on a specific device:
.\fido2-manage.exe -storage -device 2 -
Retrieve all relying parties (domains) on a specific device:
.\fido2-manage.exe -residentKeys -device 1 -
Retrieve resident keys on a specific device for a domain:
.\fido2-manage.exe -residentKeys -device 1 -domain login.microsoft.com -
Delete a credential on a specific device:
.\fido2-manage.exe -delete -device 2 -credential Y+Dh/tSy/Q2IdZt6PW/G1A== -
Name the fingerprint stored under slot #1 as"Index_Finger":
.\fido2-manage.exe -renamefingerprint 3 -fingerprintname Index_Finger -device 1 -pin 773456 -
Set a PIN on a specific device (for new devices or after a reset):
.\fido2-manage.exe -device 1 -setPINIn no PIN is provided as a part of the command (
-pin 1323345), the tool will ask to enter the PIN twice (confirmation). In case PIN lentgh or complexity requirements are not met a FIDO_ERR_PIN_POLICY_VIOLATION will be shown -
Change a PIN on a specific device:.\fido2-manage.exe -device 1 -changePINThe tool will ask to enter the current PIN and the PIN twice (with confirmation). In case PIN lentgh or complexity requirements are not met a FIDO_ERR_PIN_POLICY_VIOLATION will be shown
Enforce user verification to be always requested on a specific device:
.\fido2-manage.exe -device 1 -uvsThe tool will prompt the user to enter the current PIN if the parameter is being changed (i.e., if user verification has not already been enabled). If a PIN is not required, it indicates that the command will not alter anything. Please note that this feature is available for FIDO2.1 keys (and not FIDO2.1.PRE or earlier). If the key does not support enforcing user verification, an error will be returned ("
config_always_uv: option not found")
To disable enforcing user verification, issue the command below:.\fido2-manage.exe -device 1 -uvd
Warning
Deleting a credential is irreversible. The tool will ask for confirmation before proceeding with deletion.
Good to Know
- The FIDO2 Token Management Tool (
fido2-manage.exe) is versatile and can be used with any FIDO2 keys, not limited to those purchased from our company. This flexibility allows users to manage and interact with a wide range of FIDO2 devices, enhancing the tool's usability across different hardware providers. - When using the
-listparameter to display available devices, it's important to note that in some cases, the tool may show the platform authenticator or Windows Hello as a separate key. However, due to technical limitations, these keys cannot be managed using this tool. - The tool is primarily designed for managing traditional external FIDO2 devices. If you encounter platform authenticators or Windows Hello in the list, be aware that they fall outside the tool's scope for management operations.

Users should rely on the respective platform settings for managing these types of authenticators. - For all tool operations, it is imperative to run
fido2-manage.exein administrator mode. Open the command prompt as an administrator and navigate to the directory containing the tool to execute commands successfully.
- Whether you have FIDO2 keys from our company or another vendor, the tool provides a standardized command-line interface for performing various operations, such as listing available devices, retrieving information, managing storage, and more.
- Make sure to follow the appropriate device-specific guidelines and security practices, especially when dealing with sensitive operations like setting or changing PINs and deleting credentials.
Download
This tool is part of the fido2-manage.cpp project, which includes both a command-line utility and a GUI wrapper. The project is fully open-source.
Version History
- 0.2.3R3 (03-06-2025): Allow renaming fingerprint titles
- 0.2.3 (22-11-2024): Allow setting new PIN and forcing PIN change without an interactive prompt
- 0.2.2.2 (18-07-2024): Added PIN change enforcement and fingerprint management for biometric keys
- 0.2.2.1 (07-06-2024): Showing UPN in the passkeys table and partial support for extended Latin chars (umlauts)
- 0.2.2 (30-04-2024): Enforcing user verification parameters added (-uvs and -uvd)
- 0.2.1 (22-04-2024): PIN Code special characters escape
- 0.2 (13-04-2024): NFC Support.
- 0.1 (01-12-2023): Initial version.
Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!
