Configuring Microsoft Azure MFA on-premises server to work with Token2 classic tokens
Microsoft Azure MFA on-premises server supports time-based OATH compliant TOTP) third-party tokens, including Token2 C202 and OTPC-N1 tokens. The tokens can be added or imported prior to being associated with a user. Administrators can associate users and tokens in the Multi-Factor Authentication Server or the User Portal. Users can associate themselves with an OATH token during User Portal enrollment or use the OATH Token menu option when the User Portal is configured to provide this functionality. A bulk token import and configuration are also supported by MFA Server. An administrator can import OATH Token records from an input file. The secret keys must be in Base32 format.Requirements:
The following are the pre-requirements to complete this configuration.
- Microsoft Azure MFA on-premises server
- A Token2 classic hardware token
- Secret Key for your token device. You will receive an email with Secret Key after the purchase.
Azure MFA Server – Configuration for third Party OATH
The first step in this process is to add third-party OATH Tokens in Azure MFA Server. You can either add these tokens individually or perform a bulk import using an input file. To add an OATH token,
- Login to your MFA application server. Open Multi-Factor Authentication Server UI and Select OATH Token icon
- Click Add option from OATH Token window
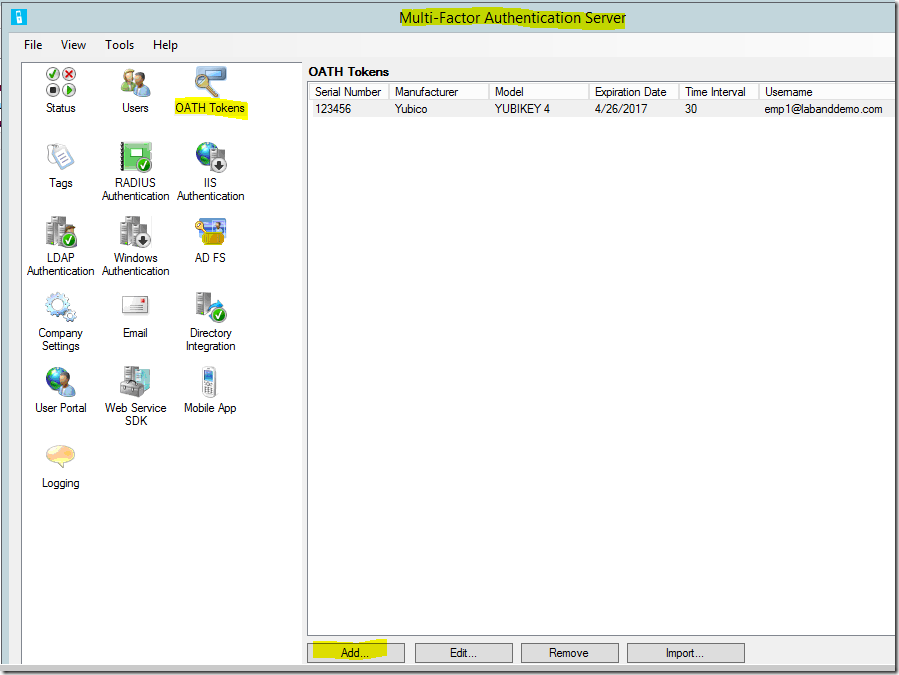
- Enter your Secret Key token Details
- Serial Number – Required. Enter the serial number of your Token2 token.
- Secret Key – Required. This is the Secret Key (Base32). You have to receive this information from Token2. You will receive an email from Token2 with Secret Key after the purchase
- Manufacturer – Optional. Enter Token2 as the manufacturer.
- Model – Optional. Enter Token2 Classic as model type.
- Start date – Optional
- Expiration date – Optional
- Time interval – Required. Select 30 seconds.
- Username: Associate a user with this OATH token. You can manually enter the username or Select User option to identify a user.
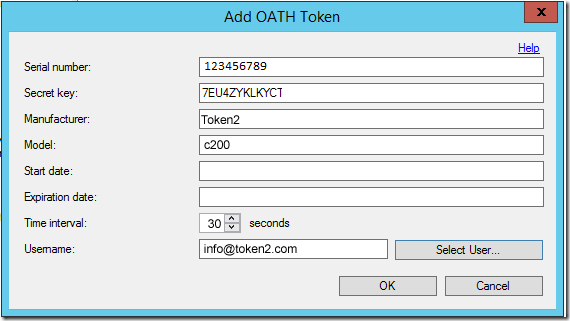
- Click OK to complete. The Synchronize OATH Token dialog will prompt for the current OATH code to synchronize the OATH token and verify the configuration
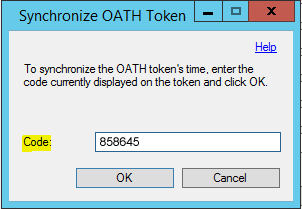
- Enter the current code from Token2 token to the Synchronize OATH Token window to complete token configuration in MFA Server. Click OK.
MFA server validates the OATH code against the OATH token secret key and synchronizes the OATH token's time if they are valid.
Bulk import using Portable Symmetric Key Container (PSKC) or CSV file is also possible. Contact us if you need assistance with bulk import.
Classic tokens with Entra ID
Other Entra ID/MS365 Guides
Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!
